Demyst data provider certification
Leading compliance and diligence framework
About this guideWhen integrating a data provider, Demyst can perform a certification on your behalf, to accelerate the time to launch a new product. This certification process includes multiple steps such as diligence, ethical and security review.
Certification overview
Overview of the Demyst certification process
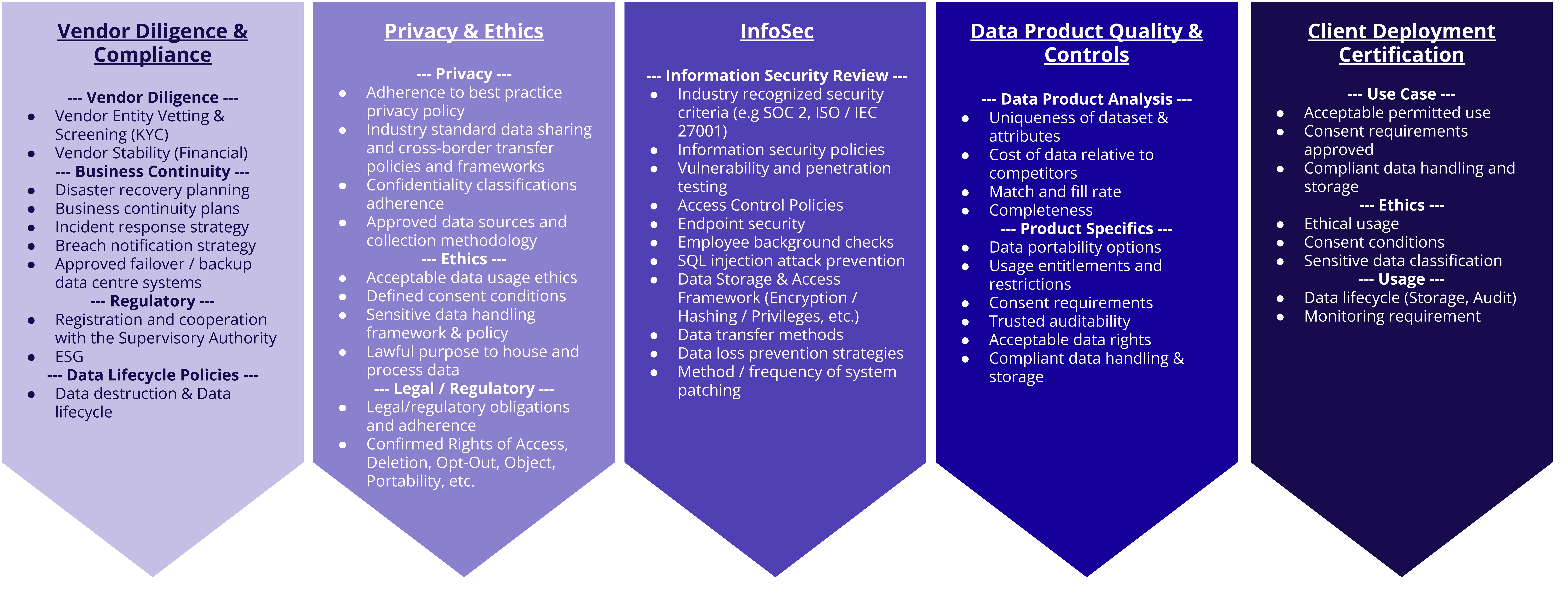
Components of the certification
Vendor diligence & compliance
Vendor Diligence
- Vendor Entity Vetting & Screening (KYC)
- Vendor Stability (Financial)
Business Continuity
- Disaster recovery planning
- Business continuity plans
- Incident response strategy
- Breach notification strategy
- Approved failover / backup data centre systems
Regulatory
- Registration and cooperation with the Supervisory Authority
- Environmental, social, and corporate governance (ESG)
Data Lifecycle Policies
- Data destruction & Data lifecycle
Privacy & ethics
Privacy
- Adherence to best practice privacy policy
- Industry standard data sharing and cross-border transfer policies and frameworks
- Confidentiality classifications adherence
- Approved data sources and collection methodology
Ethics
- Acceptable data usage ethics
- Defined consent conditions
- Sensitive data handling framework & policy
- Lawful purpose to house and process data
Legal / Regulatory
- Legal/regulatory obligations and adherence
- Confirmed Rights of Access, Deletion, Opt-Out, Object, Portability, etc.
Infosec
- Industry recognized security criteria (e.g SOC 2, ISO / IEC 27001)
- Information security policies
- Vulnerability and penetration testing
- Access Control Policies
- Endpoint security
- Employee background checks
- SQL injection attack prevention
- Data Storage & Access Framework (Encryption / Hashing / Privileges, etc.)
- Data transfer methods
- Data loss prevention strategies
- Method / frequency of system patching
Data Product Quality & Controls
Data Product Analysis
- Uniqueness of dataset & attributes
- Cost of data relative to competitors
- Match and fill rate
- Completeness
Product Specifics
- Data portability options
- Usage entitlements and restrictions
- Consent requirements
- Trusted auditability
- Acceptable data rights
- Compliant data handling & storage
Client Deployment Certification
Use Case
- Acceptable permitted use
- Consent requirements approved
- Compliant data handling and storage
Ethics
- Ethical usage
- Consent conditions
- Sensitive data classification
Usage
- Data lifecycle (Storage, Audit)
- Monitoring requirement
Updated 7 months ago